Arbitrary Letter Substitution
Introduction
With the Caesar Shift, there was a pattern to the cipher alphabet. It was this pattern that makes the cipher so easy to crack. Even by hand, it wouldn't take too long to work out which shift had been used. If there is no pattern to the cipher alphabet, the cipher is slightly more time-consuming to crack.
In the following table, the cipher alphabet has been made by placing letters from the alphabet in no particular order.
| Plain | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| Cipher | G | R | H | T | F | J | M | U | L | X | O | Q | Y | A | E | D | W | P | V | N | S | C | I | Z | B | K |
Once the cipher alphabet is constructed, the process of encryption is exactly the same as for the Caesar cipher, replace each letter with the one underneath in the table.
THE SECRET IS OUT
NUF VFHPFN LV ESN
Programming The Cipher
The following pseudocode describes an algorithm that implements this cipher.
cipherAlphabet ← "GRHTFJMULXOQYAEDWPVNSCIZBK"
plain ← "The secret is out."
upper ← UPPERCASE(plain)
cipherText ← ""
FOR letter ← 0 TO upper.LENGTH - 1
tmpASC ← ASCII CODE OF upper[letter]
IF tmpASC > = 65 AND tmpASC <= 90 THEN
cipherText ← cipherText + cipherAlphabet[tmpASC-65]
ELSE
cipherText ← cipherText + upper[letter]
END IF
END FOR
OUTPUT cipherText
Challenges
The pseudocode is useful for writing a program that encrypts a message. You could get the program to make a random cipher alphabet and output it along with the encrypted message.
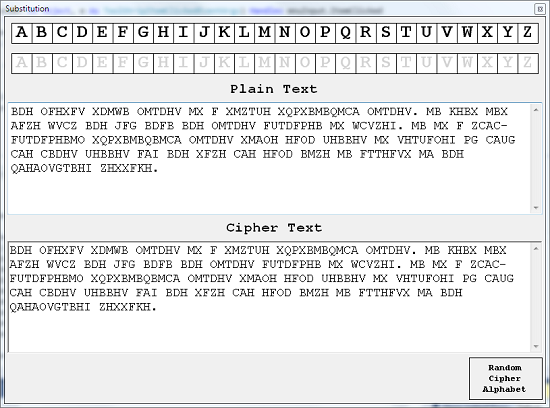
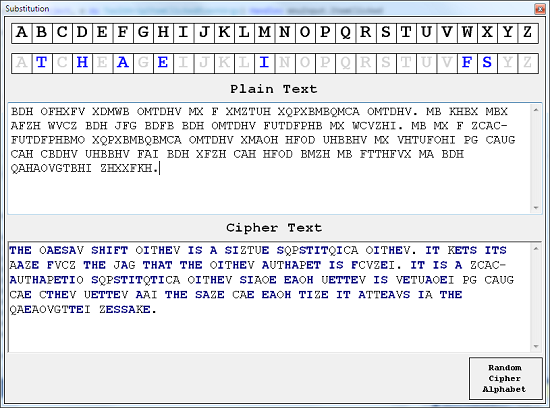
Cracking this type of cipher is all about processing. A find and replace approach allows you to try out letters in different positions in the cipheralphabet. The following screenshots show a program that allows you to do that with a simple user interface. Right mouse clicking on the letters in the cipher alphabet allows the user to change the letter. The message is automatically updated with replaced letters shown in blue. Make something like this and it is easy to solve a message witht the original spacings left in.