Caesar Shift Cipher
Introduction
The Caesar Shift cipher is a simple substituion cipher. It gets its name from the way that the cipher alphabet is formed. It is a mono-alphabetic substitution cipher since each letter is replaced by only one other letter and the same one each time it appears in the unencrypted message.
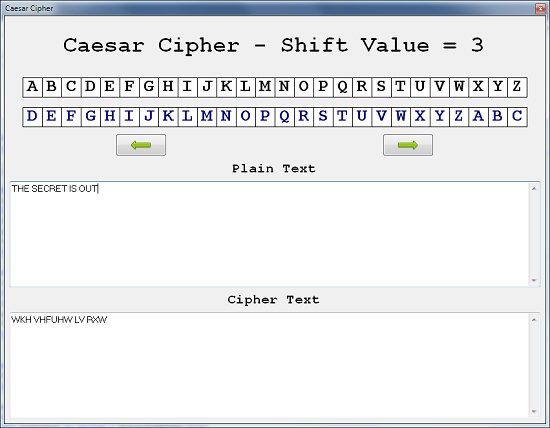
The table shows a plain alphabet on the top row. The alphabet on the bottom row has been shifted 3 places to the right.
| Plain | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| Cipher | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z | A | B | C |
To encrypt a message, replace every letter in the message with the one shown below it in the table. For example,
THE SECRET IS OUT
WKH VHFUHW LV RXW
Using a Caesar Shift of +3, each letter of the plain text message is replaced with the letter 3 places to the right in the alphabet.
Programming The Caesar Shift
The following pseudocode describes an algorithm for performing a Caesar Shift. It begins by converting the plain text message to upper case. This makes the process a little simpler. It then reads each character from the upper case plain text and examines the character's ASCII code. If the ASCII number denotes an upper case letter, it is shifted by the value of the variable shift and added to the cipher text variable. If the character is not a letter, it is added to the cipher text as it is.
plain ← "The secret is out."
shift ← 3
upper ← UPPERCASE(plain)
cipherText ← ""
FOR letter ← 0 TO upper.LENGTH - 1
tmpASC ← ASCII CODE OF upper[letter]
IF tmpASC > = 65 AND tmpASC <= 90 THEN
tmpASC ← tmpASC + shift
IF tmpASC<65 THEN tmpASC ← tmpASC + 26
IF tmpASC>90 THEN tmpASC ← tmpASC - 26
cipherText ← cipherText + CHARACTER(tmpASC)
ELSE
cipherText ← cipherText + uppper[letter]
END IF
END FOR
OUTPUT cipherText
Decrypting A Message
If you multiply the shift value of an encrypted message by -1, you have the shift you need to perform to decypt the message using the algorithm above.
Cracking The Caesar Shift
If you don't know the encrypted message's shift value but know that it was encrypted with a Caesar Shift, then simply run all of the possible Caesar shifts and look to see which message is readable.
Challenges
You can use the pseudocode to knock up a quick console based program. Once you've done that, you may want to reuse the code to make a nice interface for speedy encryption and decryption. Something looking a bit like the screenshot might be nice,
The method the algorithm uses to encrypt a message is focused on shifting the letters and does not do enough to make the message secret. Taking out the spaces and other characters is probably better than leaving them in. Another approach is to take out all of the spaces and then add a space every 4 or 5 letters.